| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | ||||||
| 2 | 3 | 4 | 5 | 6 | 7 | 8 |
| 9 | 10 | 11 | 12 | 13 | 14 | 15 |
| 16 | 17 | 18 | 19 | 20 | 21 | 22 |
| 23 | 24 | 25 | 26 | 27 | 28 | 29 |
| 30 |
- spring annotation
- monitorjbl 엑셀
- 전자서명개발
- poi monitorjbl
- mysql
- swift 계산기
- Xcode
- opcpackage
- js 전자서명
- outofmemoryerror 방지
- xcode12.5.1
- fullcalendar js
- Swift
- MSsql
- 달력기능개발
- PostgreSQL
- ios app 개발
- Oracle
- jxls
- xcode swift memo
- js달력
- xssreader
- swift 메모장 만들기
- poi 대용량
- xlsx-streamer
- jxls 엑셀
- monitorjbl
- xssfworkbook
- 전자서명기능구현
- 대용량엑셀업로드
- Today
- Total
web developer👩🏻💻
로그인 양방향 암호화(RSA) 단방향 암호화(SHA 256) 사용하기 본문
양방향 암호화(RSA) 단방향 암호화(SHA 256) 차이
| RSA | SHA 256 |
| 양방향 암호화 = 복호화가 가능하다. | 단방향 암호화 = 복호화가 불가능하다. |
| 사용자는 공개된 키와 자신만 아는 개인키를 가진다. | hash 함수의 일종 |
| 공개키, 개인키로 암호화/복호화를 하는 시스템 | SHA 알고리즘의 한 종류로 256비트로 구성 64자리 문자열을 반환 |
| 키생성 - 키분배 - 암호화 - 복호화 순으로 이루어짐. | 복호화를 하지 않아도 되 속도가 빠르다. |
web(JSP) -> server(controller)로 파라미터를 보낼 때 중간에서 정보를 가로챌 수 있다.
이러한 보안 문제를 막기 위해 JSP에서 RSA를 사용하여 비밀번호를 암호화해준다..
RSA로 암호화된 파라미터를 controller에서 복호화시키고,
복호화시킨 파라미터 값을 단방향 암호화인 SHA256으로 암호화시킨다.
RSA 암호화
Rsa.java
package egovframework.let.utl.sim.service;
import java.security.KeyFactory;
import java.security.KeyPair;
import java.security.KeyPairGenerator;
import java.security.PrivateKey;
import java.security.PublicKey;
import java.security.spec.RSAPublicKeySpec;
import javax.crypto.Cipher;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpSession;
public class Rsa {
public static String RSA_WEB_KEY = "_RSA_WEB_Key_"; // 개인키 session key
public static String RSA_INSTANCE = "RSA"; // rsa transformation
/**
* 복호화
*
* @param privateKey
* @param securedValue
* @return
* @throws Exception
*/
public String decryptRsa(PrivateKey privateKey, String securedValue) throws Exception {
Cipher cipher = Cipher.getInstance(Rsa.RSA_INSTANCE);
byte[] encryptedBytes = hexToByteArray(securedValue);
cipher.init(Cipher.DECRYPT_MODE, privateKey);
byte[] decryptedBytes = cipher.doFinal(encryptedBytes);
String decryptedValue = new String(decryptedBytes, "utf-8"); // 문자 인코딩 주의.
return decryptedValue;
}
/**
* 16진 문자열을 byte 배열로 변환한다.
*
* @param hex
* @return
*/
public static byte[] hexToByteArray(String hex) {
if (hex == null || hex.length() % 2 != 0) { return new byte[] {}; }
byte[] bytes = new byte[hex.length() / 2];
for (int i = 0; i < hex.length(); i += 2) {
byte value = (byte) Integer.parseInt(hex.substring(i, i + 2), 16);
bytes[(int) Math.floor(i / 2)] = value;
}
return bytes;
}
/**
* rsa 공개키, 개인키 생성
*
* @param request
*/
public void initRsa(HttpServletRequest request) {
HttpSession session = request.getSession();
KeyPairGenerator generator;
try {
generator = KeyPairGenerator.getInstance(Rsa.RSA_INSTANCE);
generator.initialize(1024);
KeyPair keyPair = generator.genKeyPair();
KeyFactory keyFactory = KeyFactory.getInstance(Rsa.RSA_INSTANCE);
PublicKey publicKey = keyPair.getPublic();
PrivateKey privateKey = keyPair.getPrivate();
session.setAttribute(Rsa.RSA_WEB_KEY, privateKey); // session에 RSA 개인키를 세션에 저장
RSAPublicKeySpec publicSpec = (RSAPublicKeySpec) keyFactory.getKeySpec(publicKey, RSAPublicKeySpec.class);
String publicKeyModulus = publicSpec.getModulus().toString(16);
String publicKeyExponent = publicSpec.getPublicExponent().toString(16);
request.setAttribute("RSAModulus", publicKeyModulus); // rsa modulus 를 request 에 추가
request.setAttribute("RSAExponent", publicKeyExponent); // rsa exponent 를 request 에 추가
} catch (Exception e) {
// TODO Auto-generated catch block
e.printStackTrace();
}
}
}login.jsp
RSA 양방향 암호화를 사용하기 위해선 RSA 자바스크립트 라이브러리 추가가 필요하다.
여기서 js를 다운로드 받아 프로젝트에 넣는걸 추천.
JSEncrypt
Introduction When browsing the internet looking for a good solution to RSA Javascript encryption, there is a whole slew of libraries that basically take the fantastic work done by Tom Wu @ http://www-cs-students.stanford.edu/~tjw/jsbn/ and then modify that
travistidwell.com
<script type="text/javascript" src="http://www-cs-students.stanford.edu/~tjw/jsbn/rsa.js"></script>
<script type="text/javascript" src="http://www-cs-students.stanford.edu/~tjw/jsbn/jsbn.js"></script>
<script type="text/javascript" src="http://www-cs-students.stanford.edu/~tjw/jsbn/prng4.js"></script>
<script type="text/javascript" src="http://www-cs-students.stanford.edu/~tjw/jsbn/rng.js"></script>// 비밀번호 암호화
function frm_check(){
var pw = document.loginForm.password.value;
// rsa 암호화
var rsa = new RSAKey();
rsa.setPublic($('#RSAModulus').val(),$('#RSAExponent').val());
$("#password").val(rsa.encrypt(pw));
}서버 측에서 RSA 공개키와 개인키(암호키)를 생성하여 개인키는 세션에 저장하고 공개키는 HTML 로그인 폼 페이지에 Input [type=hidden] value 값에 세팅.
<form:form id="loginForm" name="loginForm" action="${pageContext.request.contextPath}/actionLogin.do" method="post" onsubmit="return frm_check();" >
<div class="user_login_ultop">
<input type="hidden" id="RSAModulus" value="${RSAModulus}"/>
<input type="hidden" id="RSAExponent" value="${RSAExponent}"/>
<ul>
<li>
<label for="id"></label>
<input type="text" class="input_style" title="아이디를 입력하세요." id="id" name="id" maxlength="10"/>
</li>
<li>
<label for="password"></label>
<input type="password" class="input_style" maxlength="25" title="비밀번호를 입력하세요." id="password" name="password"/>
</li>
<li>
<input type="checkbox" name="checkId" id="checkId" /><label for="checkId">ID저장</label>
</li>
</ul>
<input type="submit" alt="로그인 하기" value="로그인" class="btn_style"/>
</div>
</form:form>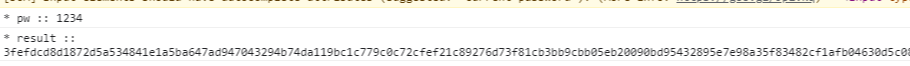
RSA 복호화
LoginController.java
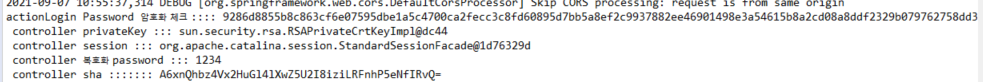
Rsa r = new Rsa();
HttpSession session = request.getSession();
//로그인전에 세션에 저장된 개인키를 가져온다.
PrivateKey privateKey = (PrivateKey) session.getAttribute(Rsa.RSA_WEB_KEY);
//암호화 된 비밀번호를 복호화 시킨다.
String password = r.decryptRsa(privateKey, LoginVO.getPassword());
// ShA 256 암호화 = 단방향
String sha = EgovFileScrty.encryptPassword(password);
LoginVO.setPassword(sha);SHA 256 암호화
EgovFileScrty.java
/**
* 비밀번호를 암호화하는 기능(복호화가 되면 안되므로 SHA-256 인코딩 방식 적용).
*
* deprecated : 보안 강화를 위하여 salt로 ID를 지정하는 encryptPassword(password, id) 사용
*
* @param String data 암호화할 비밀번호
* @return String result 암호화된 비밀번호
* @exception Exception
*/
@Deprecated
public static String encryptPassword(String data) throws Exception {
if (data == null) {
return "";
}
byte[] plainText = null; // 평문
byte[] hashValue = null; // 해쉬값
plainText = data.getBytes();
MessageDigest md = MessageDigest.getInstance("SHA-256");
hashValue = md.digest(plainText);
return new String(Base64.encodeBase64(hashValue));
}
참고 :
GitHub - kenu/egov
Contribute to kenu/egov development by creating an account on GitHub.
github.com
RSA (비대칭 암호화 알고리즘)
사용하는 목적WEB 서버에 SSL 설치 없이 로그인처리할때 평문으로 전송할경우 중간에서 정보를 가로채어 가로챈 계정정보를 권한이 없는 사용자가 시스템에 로그인 한후 시스템을 손상시킬수도
velog.io
'Spring' 카테고리의 다른 글
| [EgovFramework] Spring Interceptor session AJAX 처리 (0) | 2021.10.18 |
|---|---|
| [EgovFramework] context-syslogaop.xml aop Error (0) | 2021.10.12 |
| [Spring Error] Can not find the tag library descriptor for (0) | 2021.08.31 |
| [JAVA] Lamda 표현식 예제 (0) | 2021.08.27 |
| [MAVEN] java.util.zip.ZipException: invalid LOC header (bad signature) 오류 (0) | 2021.08.12 |



